IT managers do not FEEL secure with their cyber security program
KELA surveyed 400 security team members in the US who were responsible for gathering cybercrime threat intelligence daily
54%
wouldn’t be surprised to find their organization’s data on the underground.
49%
are not satisfied with the visibility they have of the cybercrime underground.
59%
of respondents do not believe their current cybercrime prevention program is very effective.

Is your enterprise under constant threat?
Become proactive with THREAT INTELLIGENCE
ZERO IN ON THE TRUE THREATS Before they HIT
Extreme Targeting
Curated Sources
Automation & Service
What does KELA offer?

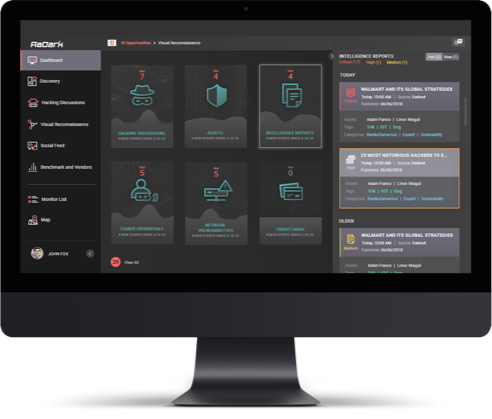
INTELLIGENCE POINT OF VIEW
KELA’s process of gathering and analyzing data emulates the thought-process of a hacker prior to an attack.
MULTILINGUAL TEAM
While KELA’s technologies monitor intelligence in more than 100 languages, our team speaks a total of more than 20, all common in Darknet communities.
HUNDREDS OF CURATED SOURCES
Our analysts scan and handpick new information sources daily, ensuring all potential threats are being monitored.
TARGETED MONITORING
Highly targeted intelligence-gathering prevents any generic, redundant or low-impact threats.
REAL-TIME ACTIONABLE INTELLIGENCE
Immediate notifications and 100% actionable alerts of Darknet threats.
TECHNOLOGY & ANALYSTS
Integrating automation and manual oversight by analysts guarantees the most relevant intelligence analysis and remediation process.
