
Unified Detection & Response Built for MSPs
Streamline cybersecurity with an AI-powered platform to secure identities, endpoints, email, cloud, and data from a single pane of glass.
Unified Platform
Simplify your security management and enhance defense capabilities with an innovative AI-powered unified platform that connects the dots across M365/Google Workspace users, emails, devices, data, awareness, and more into a single backbone and provides aggregated views of detections, ensuring rapid and effective threat detection and response.
Built For MSPs
Boost Your Revenue
Attract new clients by demonstrating your reliability through efficient prospecting capabilities, accurate reporting, and complete coverage.
Real Time Detections
Designed for MSPs to toggle between clients, prioritize risky issues, and deep dive into specific assets and detections as needed.
Show Immediate Value
Enhance your security services for your clients with just a click to seamlessly demonstrate value while delivering ongoing business reviews to show progress.
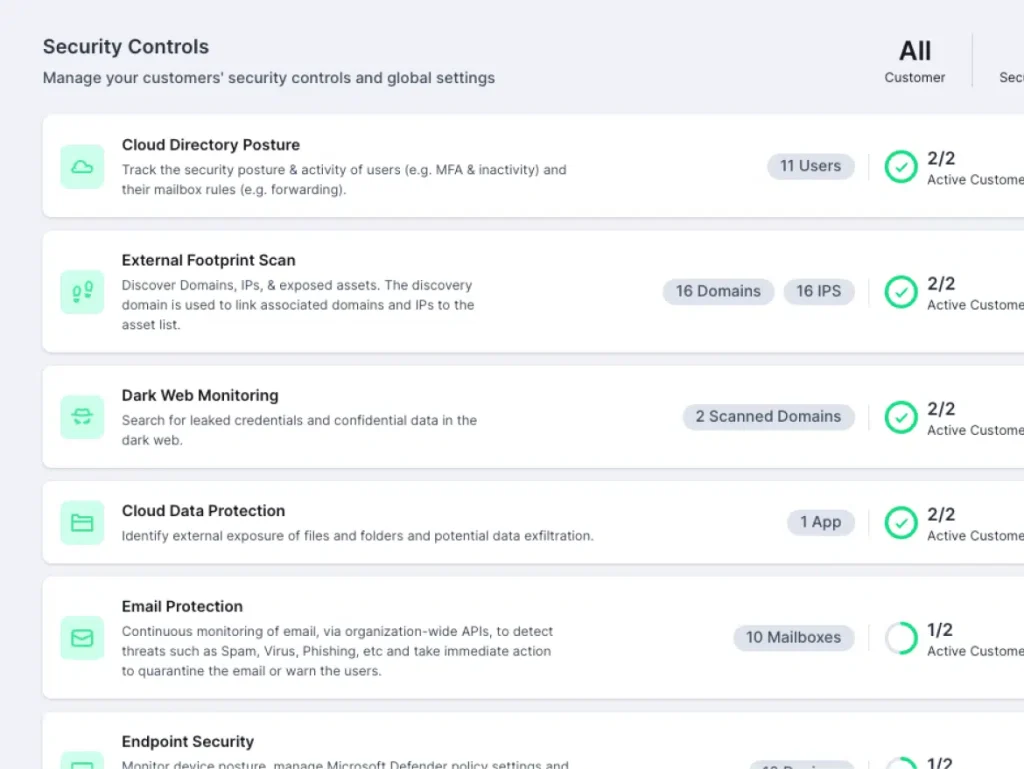
Integrated Security Controls in One Backbone
The Guardz Security Controls are a reflection of the holistic approach to cybersecurity, putting the core safeguards in one place while simplifying the setup and management of these critical controls.
This centralized view of Guardz Security Controls enables hassle-free configuration for each control, ultimately simplifying security implementation and issue resolutionin a breeze.
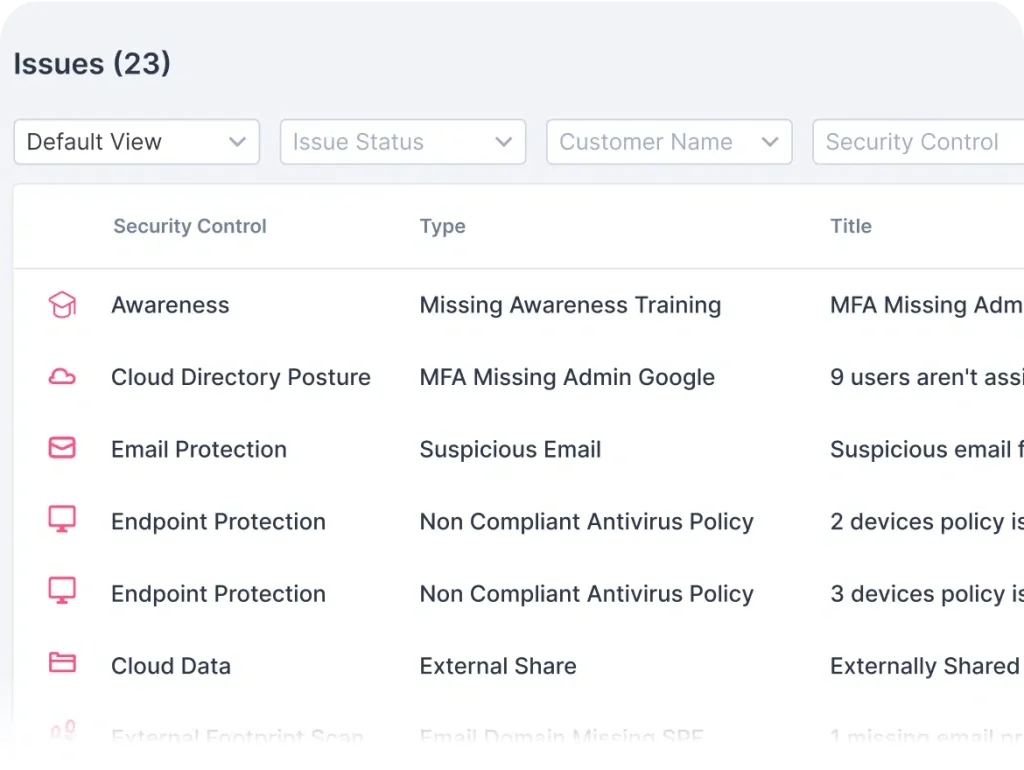
Single View of All Issues
Guardz continuously scans for threats across multiple attack vectors and generates issues when a threat is detected. Issues are prioritized by severity of risk and include all the relevant details to trigger automated and manual remediations.
See more specific information about the issue, choose the most suitable remediation, and complete the action to resolve the issue.
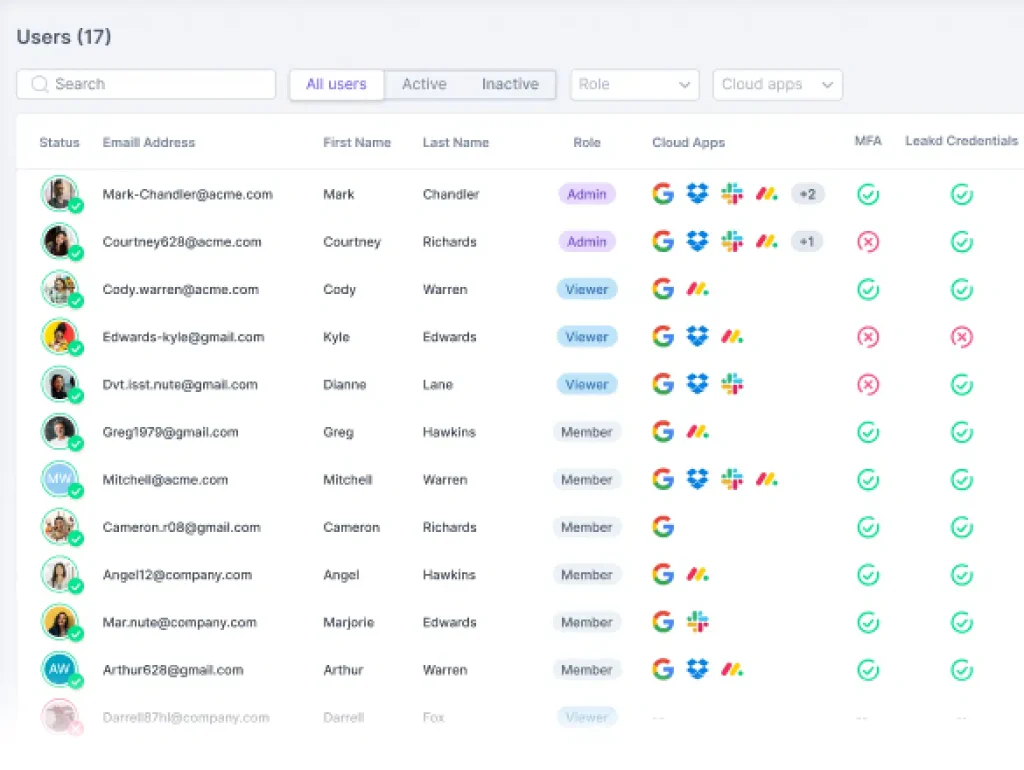
Users are the First Line of Defense
Users are at the center of defining an organization’s risk, so Guardz aggregates user-level data to paint a picture of employee risk and its impact on the company.
A company’s cloud directory (Google or Microsoft) is the source of the user list and is enriched with data about licensing, role, cloud apps, issue status, related devices, and more.
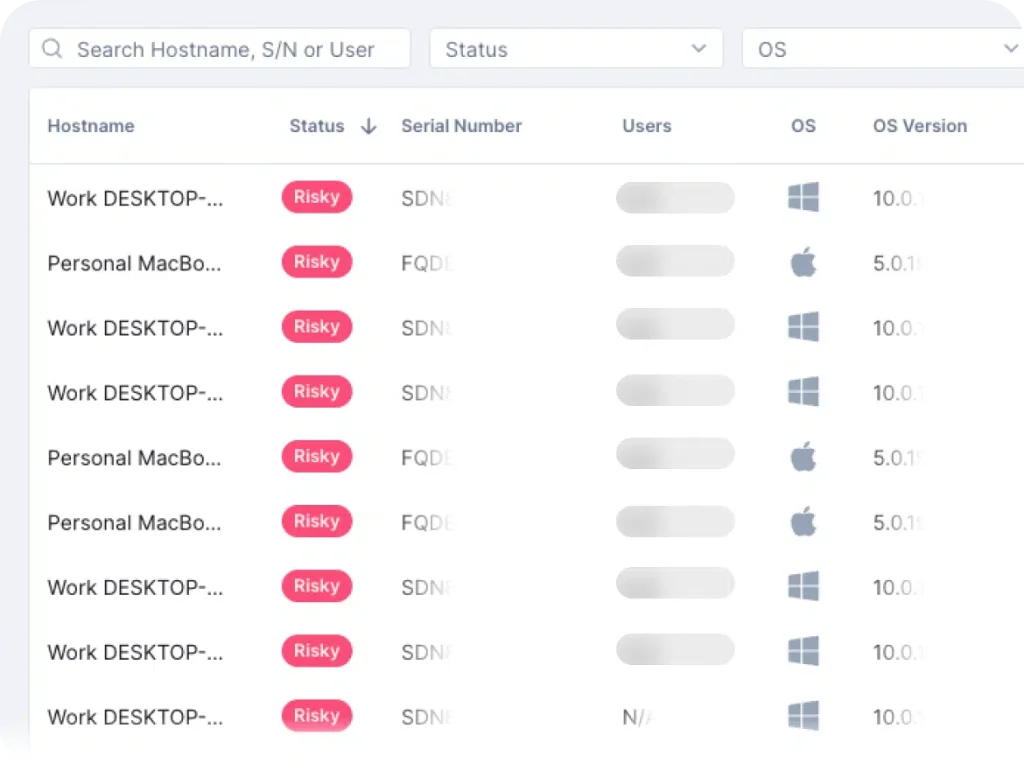
Secure All Devices
The simplified device management feature offers visibility into devices across an organization, providing vital information on their health status, relevant metrics, threat/risk levels, and existing issues.
This enhances the management of a company’s antivirus capabilities and streamlines the process of addressing device-related concerns.
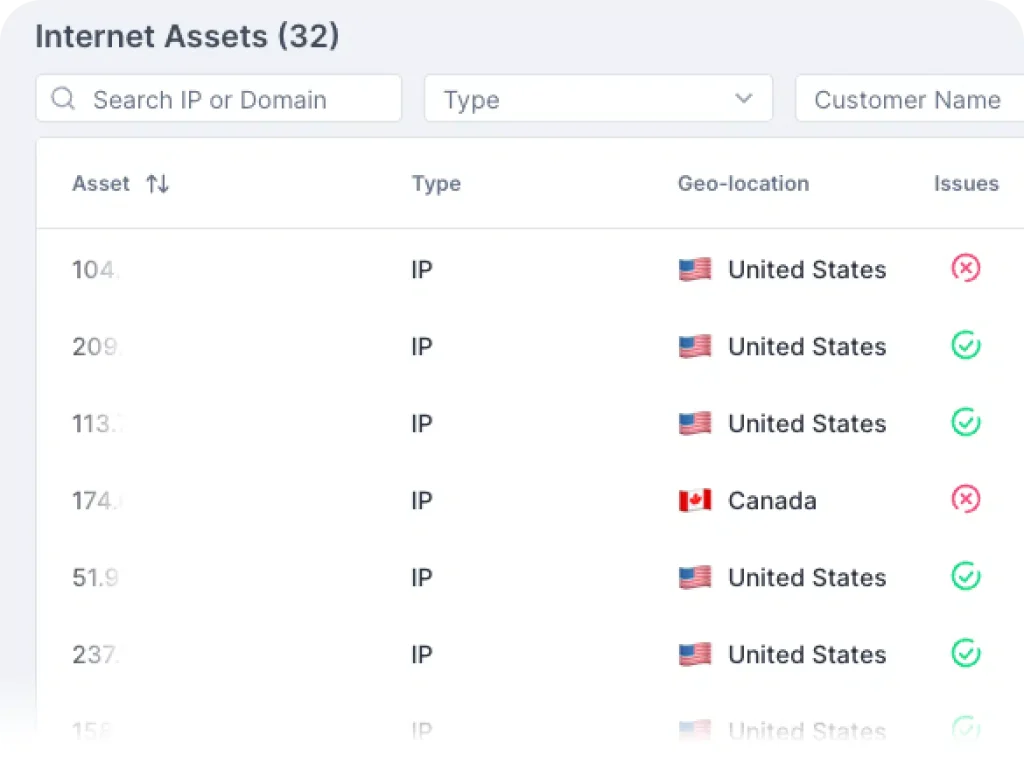
Full Visibility of Digital Footprint
Attackers exploit weak points in the organization’s network, often left unprotected. The Guardz External Footprint Scan helps you to discover, manage, and monitor your organization’s assets in one place.
Upon initial sign-up, Guardz will run a scan automatically on all assets related to your primary domain (domains, sub-domains, and IPs) and discover all the connected assets.
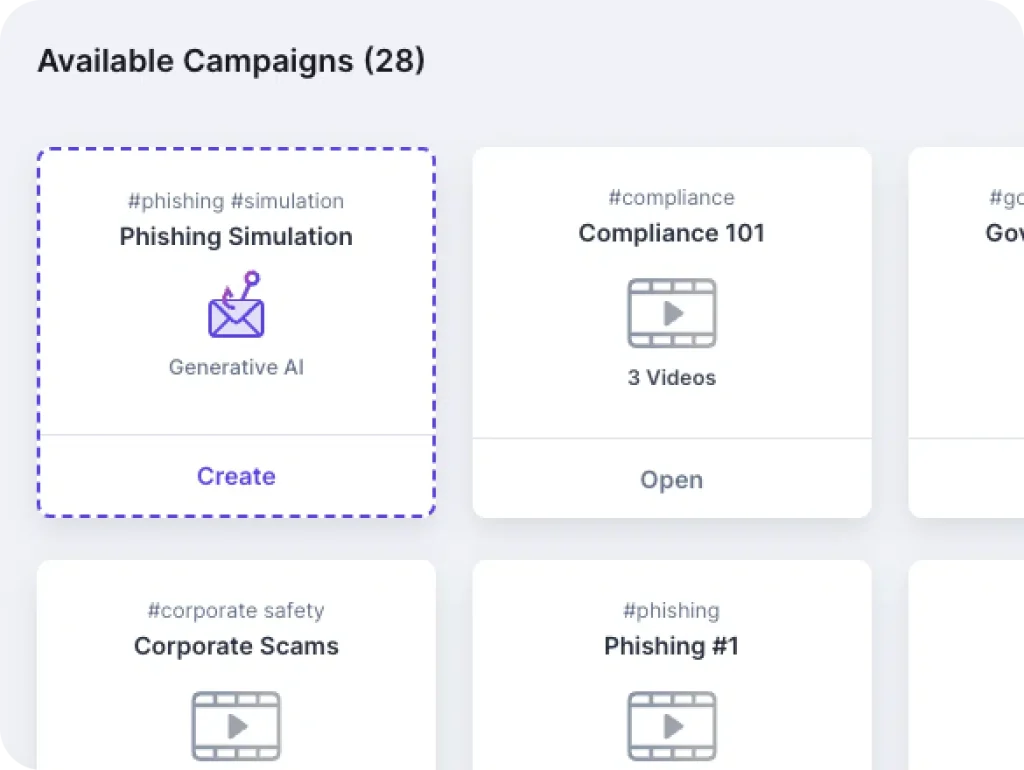
Building Awareness Culture
Guardz ensures up-to-date employee training by notifying admins of training status and recommending industry-standard best practices. Customizable campaign planning allows businesses to target specific users and meet company goals.
Phishing simulations help employees learn to avoid threats like ransomware and malware, while mandatory evaluations measure the impact of training.

Gain Admin Rights Compliance
With rapid provisioning of Just-In-Time privilege elevation across your entire workforce. On-board and manage workstations and servers via a user-friendly portal.

Monitor and Audit Behavior
To reveal risky users and assets through thread and behavioral analytics to identify malicious software and prevent data breaches and malware attacks.

Enhance User Productivity
By elevating applications – not users. Delegate privileges based on the user or groups to save time and monetary resources.
