
Monitor, Hunt and Mitigate Cyber Crimes with Real Intelligence.
Automatically uncover your attack surface by leveraging attackers’ perspectives for proactive protection.
SECURE THE UNSEEN - NO MORE BLIND SPOTS
KELA’s Comprehensive Cyber Intelligence Platform
Neutralize risk by monitoring your case objectives and assets for your teams to get actionable intelligence that prevents crimes
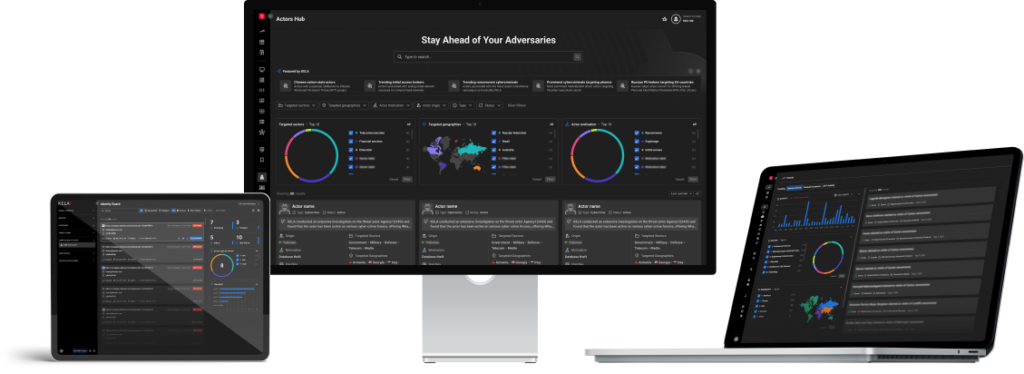
KELA’s market-leading platform penetrates the hardest-to-reach places to automatically collect, analyze, monitor and alert on emerging threats coming from the cybercrime underground.
Based on the unique, historical security data lake, KELA’s end-to-end cyber threat intelligence platform supports organizations in preventing potential cyber attacks by making the complex world of the cybercrime simple and accessible. It consists of several modules, each designed with a unique purpose to serve the organization’s needs.
MONITOR
Supports operational security roles by providing attack surface and asset management capabilities. It alerts on targeted threats specifically aimed at the organization by analyzing the adversary's perspective of the organization's external attack surface.
INVESTIGATE
Helps analysts to perform successful threat hunting and deepen their cyber investigations with contextualized intelligence insights as to attackers’ TTPs, threat actor profiles and identities, hacking discussions, and more.
THREAT ACTORS
Centralizes diverse web-sourced threat actor data, aids investigations, offers deep insights via a user-friendly interface, enhances decision-making, and supports proactive defense. Vital intel for security teams.
IDENTITY GUARD
Tailors proactive account protection for businesses, monitoring and detecting compromised accounts across domains using data from millions of infected machines. Categorizes incidents by severity and seamlessly integrates with other security tools for rapid responses.
THREAT LANDSCAPE
Offers decision-makers high-level intelligence on the ever-changing cybercrime ecosystem, including dashboards of top trends, daily highlights, and finished intelligence feed by KELA's cyber intelligence experts.
TECHNICAL INTELLIGENCE
Provides SOC teams with automated detection and monitoring of potentially compromised IPs and domains involved in cybercrime activity.
